Sept 10
39,000 feet over the Russian/Mongolian border
“A good traveler has no fixed plans and is not intent on arriving.” – Lao Tzu
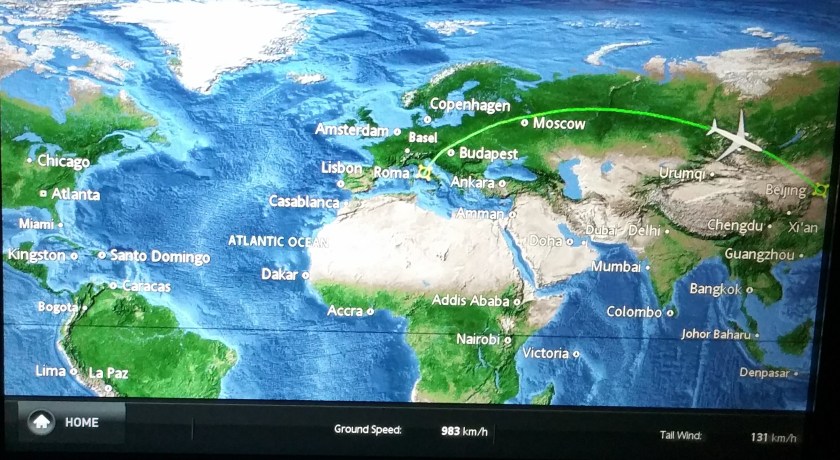
Cruising on a tailwind at just over 600 mph and near the end of my 10-hour flight from Rome to Beijing, I’ve had ample time to reflect on my journey thus far. In between moments of reflection and not being able to sleep much, I watched one of my favorite movies, Moneyball about Billy Beane and 2002 Oakland A’s – more on that later.
I also finally got a chance to catch up on emails. Most were typical read-and-delete but one was from a cyber security buddy who gave me a little good-natured ribbing as my recent posts have been light on that topic. He was in fact correct, but I have learned when one is on safari there are more important things than re-tweeting and heaping shame on the latest breach victims or how this vendor or that could have prevented it. That said, in my conversations with security experts along the way, a few classic woes continue to frame our discussions around the current state of enterprise cyber security:
- People – The shortage of skilled personnel at all levels in our profession
- Process – The continuing lack of basic security hygiene (vendors as well as practitioners)
- Technology – The emergence of artificial intelligence (AI) as a critical arrow in our cyber-quiver
Security Resources
As my UK friend and RAF veteran Simon Wilkinson put it, “It’s first about people – there are simply not enough security resources to go around.” A recent ISC2 report states that in Europe alone, the skills shortfall forecast is estimated to be over 350K by 2022. A Cisco report from 2016 put the figure of unfilled cybersecurity jobs at one million worldwide. This problem has created a significant gap between the haves and have-nots – organizations that are able to outbid for those scarce resources and those who simply cannot afford to. Companies struggling to fill jobs are turning to managed services to fill the gap. In the past, I’ve been a big proponent of managed security services where they make sense but I’m also acutely aware Cyber is not a one-size-fits-all problem. There are tangible benefits beyond staffing, such as reducing security infrastructure and software maintenance and avoiding vendor lock-in. But in turning over that function to a partner you also may trade off agility to respond to the speed of business changes, acquisitions, new systems, etc. Regardless, the skills shortfall problem is not something that can be fixed in the near term and will likely be solved through a combination of more people, better processes and advances in technology.
Security Hygiene
A recent report in Computer Business Review states 90% of business are vulnerable to hacks due to unpatched vulnerabilities dating back three years or more. Lack of basic security hygiene has been a problem for quite some time and regardless of how much technology or policy we throw at it, vulnerabilities exploited via code, architecture or lack of awareness continue to be the number one way adversaries gain access to systems. In the CBR article, Phil Quade, Fortinet CISO says, “Cybercriminals aren’t breaking into systems using new zero-day attacks; they are primarily exploiting already discovered vulnerabilities. The technology innovation that powers our digital economy creates opportunity for good and bad in cyber security. Yet, something we don’t talk about often enough is the opportunity everyone has to limit bad consequences by employing consistent and effective cyber security hygiene.” Enterprises can’t keep pace with patches and the hackers know it.
Unpatched vulnerabilities are still the “Easy Button” into our systems.
Emergence of AI
Just as artificial intelligence, specialized algorithms and the rise of Quants disrupted the trading markets, many start-ups are looking to leverage machine learning and AI to identify trends and anomalous patterns to help practitioners detect and stop unauthorized access to systems before damage is done. In addition to faster time to detection and remediation, there is promise that this approach could reduce the number of “eyes on screens” needed to appropriately staff a Security Operations Center (SOC) and thereby alleviate some pressure created by the shortage of qualified personnel. Unfortunately, the same AI technology is also being weaponized by the bad guys (namely, nation-states) in the cyber arms race.
The first two problems I think we all agree on – Mom & apple pie, right? We simply can’t mint enough qualified security experts to fill the current need any time soon. And with 2016 being a record breaking year for the number of vulnerabilities reported, this isn’t a problem that’s going away quickly either. So what about the adoption of AI and other new, cutting-edge technologies?
As I walked the floor at RSA conferences in years past, I’ve talked to plenty of security vendors hawking the next “shiny new object”. Perhaps some could actually help if we could get them fully implemented. In a 2016 survey conducted by the ISSA and the Enterprise Security Group, respondents were asked about the implications of the global cybersecurity skills shortage on their organizations. Not surprisingly, 35 percent said the skills shortage has created a situation where the staff doesn’t have time to learn the nuances of the security products they purchase, meaning these technologies are never used to their full potential. Hmm…not enough people to make our security technology work effectively…is it the chicken or the egg?
If what we’ve been doing isn’t working, do we need to start thinking about this in a different way? Is predictive analytics coupled with automated response the baby step toward autonomous, self-healing security? Can AI algorithms that mimic the human immune system be the next evolution in defending enterprise networks? Rather than bolting on more software and hardware to already vulnerable systems, should capability of this type be built into the very fabric of our networks and computing platforms? Is blockchain technology possibly the answer for finally securing transactions, especially in the IoT and even more critically, the IIoT world?
To quote my former HP colleague and friend Art Gilliland, now CEO at Skyport Systems, “There is not enough time, skill or capability for organizations to protect themselves from focused attackers. Security needs to be built in by design, not bolted on after.”
So the answer to thinking about this in a different way is certainly “yes” – and many of us already are. We may come to different conclusions on how to close our specific organizational gaps, but we know can’t continue to do the “same old thing”. Perhaps the bigger challenge for security leaders today will be getting the rest of our executive team up-to-speed and on board as well.
As I was watching Moneyball after dinner, it got me thinking about these issues. In 2002, Billy Beane was the GM of the Oakland A’s baseball team. Defying conventional wisdom, he led a completely low budget, under-staffed squad that year to the AL West Division title relying on a new, cutting-edge analytical scouting system called sabermetrics. Prior to the start of that season, he and his head scout argued over how Beane’s new approach disregarded the experience and intuition of his lifelong “baseball men” and how he would ultimately fail. Billy, given the circumstances and understanding the need to think about the problem in an entirely different way resisted, and famously responded “Adapt or die”. He then fired the scout and ultimately went on to win the division. Today, sabermetrics is the foundational scouting tool for all MLB teams.
Like Billy Beane and the A’s organization in 2002, our game is changing, as well. In order to survive in this climate of rapid business transformation coupled with the evolving nature of cyber-attacks, our collective thinking on security must mature and adapt – and quickly.
I prefer to call it “Adapt and win”.
So despite the whirlwind of planes and trains, I have managed to keep up somewhat with recent news in the security space. More importantly, I’ve been following the stories about the very devastating earthquakes in Mexico and the parade of hurricanes moving across the Caribbean and US – life changing events that will have an impact for years to come.
When it comes to security news and breaches, every-day folks I’ve talked to throughout Europe don’t seem to pay much attention. For example, most Italians I’ve met are fully aware of the earthquakes and hurricanes half a world away with many concerned enough to ask if my home or family were affected. However those not in the security profession, when asked what they knew about the Equifax breach or even recent local cyber-events, just shrugged. My observation is it’s not lack of intellectual curiosity but rather a different set of priorities that guide their day-to-day lives. Rather than being relentless slaves to the 24-hour news cycle, the people here tend to focus more on what they call the good life or “il Buona Vita”.
To paraphrase my chatty but savvy cabdriver on the way to Leonardo da Vinci airport, “I am happy you’re on a good, long holiday. Most Americans, all they do is work, work, work. Here in Italy, a person works to provide the life – family, food, a day at the beach, maybe a dance on Friday night. The life we lead, family and friends – it’s what defines us, not our job or how much money we make…”
As my Alitalia Airbus 330 slowly descends into a hazy Beijing, I am curious if I’ll encounter a similar attitude. And for my security friends, fear not – I’ll continue to share what I learn along the way but I’ll also ask for a little indulgence. Considering my next stint of “work, work, work” is likely just over the horizon, I’ve decided to heed the cabbie’s words for now and focus a little more on il Buona Vita. Cheers! -p
Next up – A Tale of Two Walls
If you’re joining in progress and curious about my trip, start here.


































































